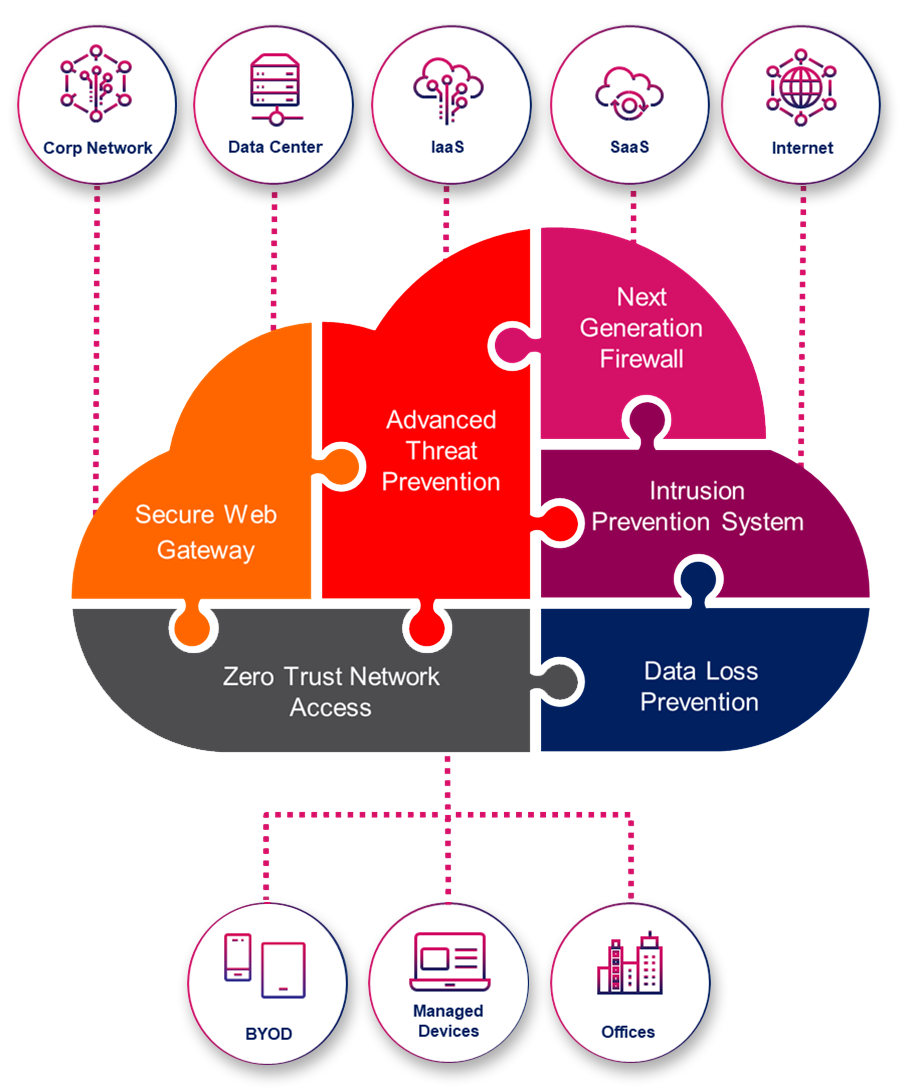
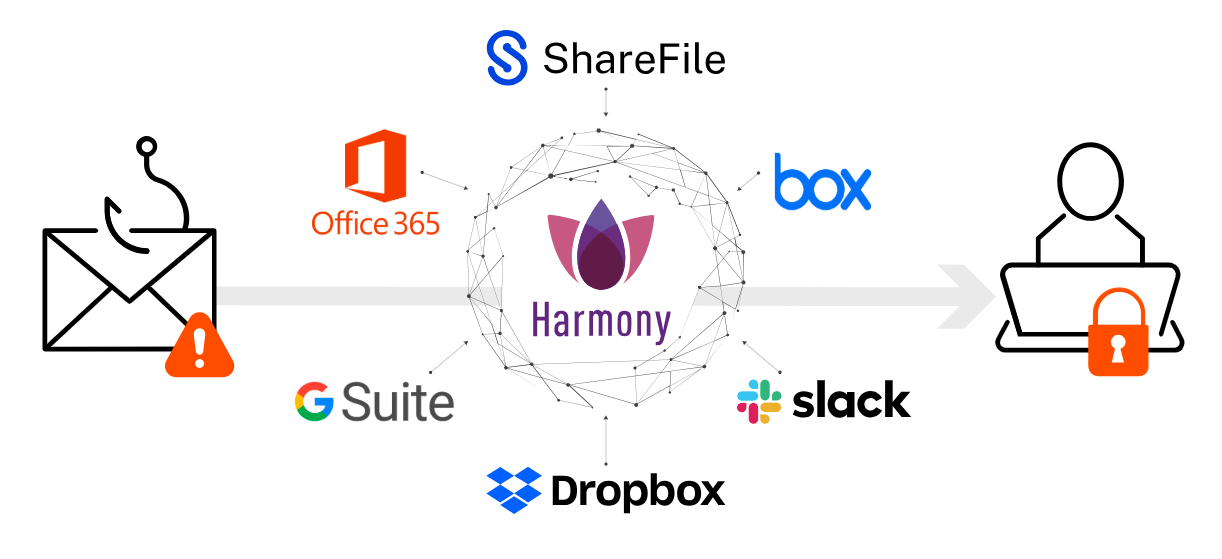
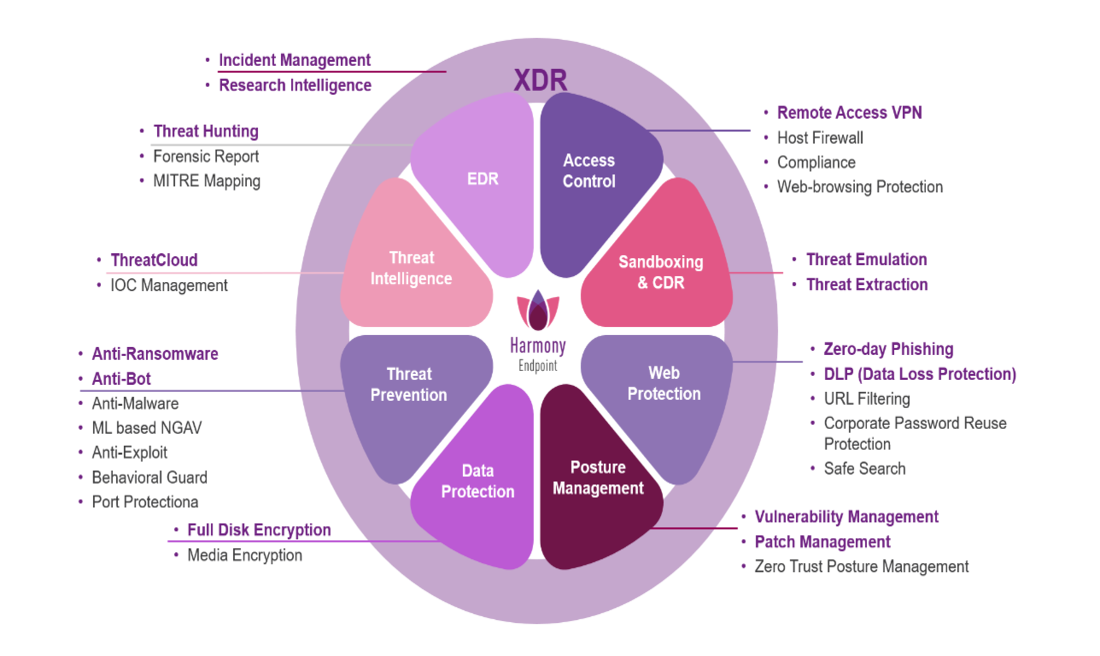
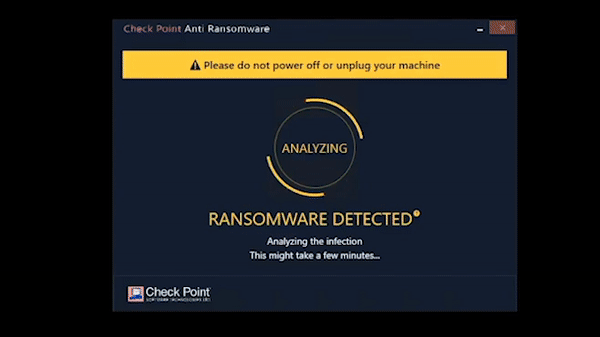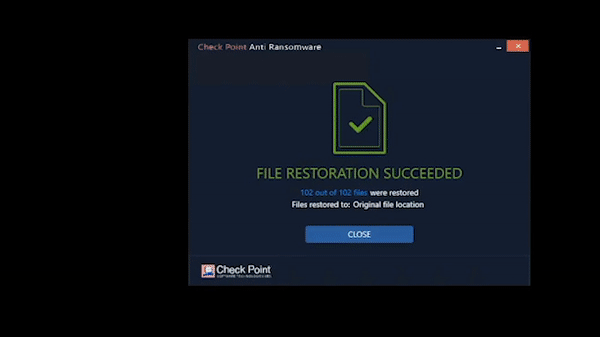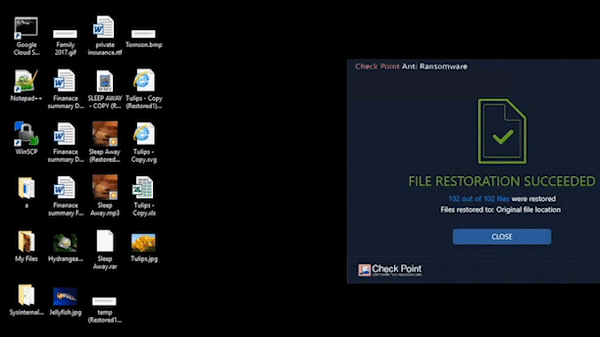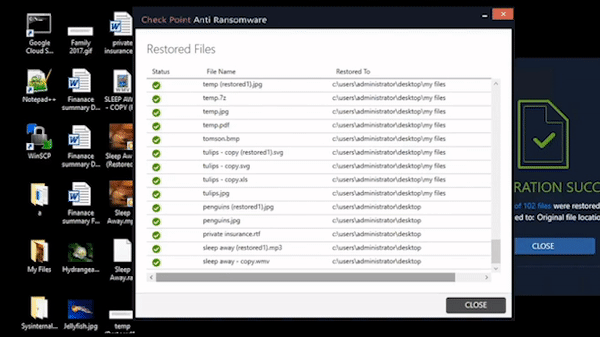
India's First Fully Managed Secure Digital Workspace Solution (HEC and HEP)
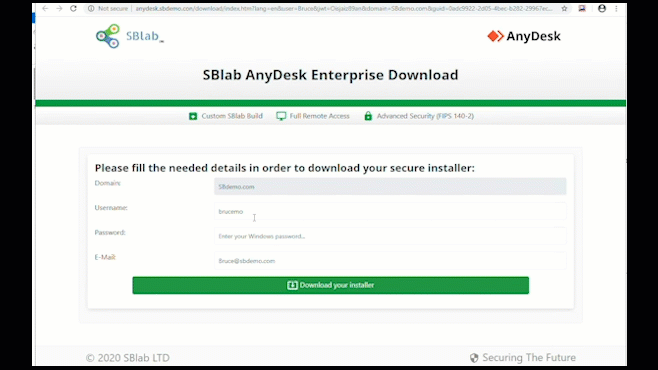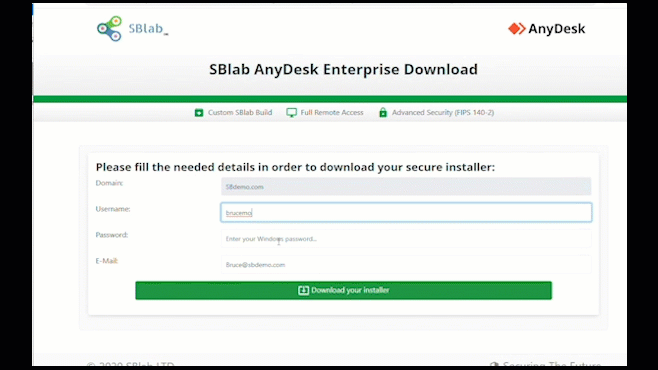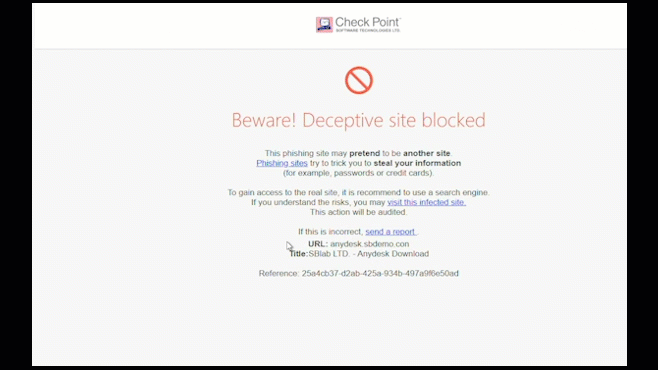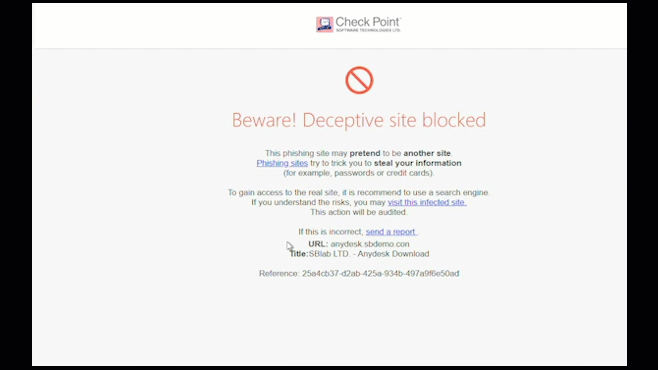
Prevents Advances Phishing Attack & Spoofing | Zero-day Email Threat Protection | Secure Browsing | Low Latency | Better App Performance Best for Hybrid Workplace | Easy Deployment